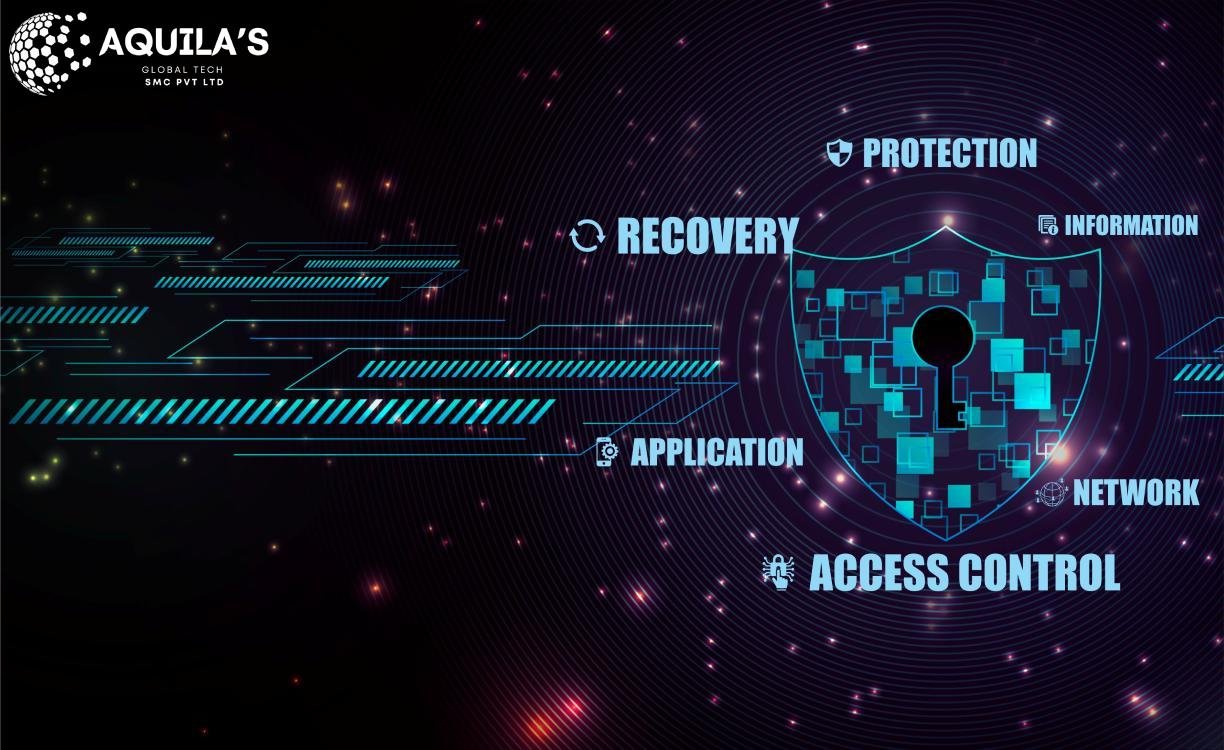
Cybersecurity threats are evolving rapidly, making it crucial for both individuals and businesses to stay vigilant. As technology advances, cybercriminals are leveraging new techniques and tools to exploit vulnerabilities, creating more sophisticated and potentially devastating threats. As we approach 2025, here are the top 10 cybersecurity threats to watch out for and actionable steps to protect yourself from them.
1. AI-Powered Cyber Attacks
Artificial intelligence (AI) is being increasingly used by cybercriminals to enhance their attacks. AI can automate the process of finding system vulnerabilities, crafting convincing phishing emails, and launching large-scale cyberattacks with remarkable speed. AI-powered tools are also able to adapt and evolve quickly, making them difficult to detect and defend against.
How to Stay Safe: Implement AI-driven security tools that can detect anomalies and unusual behaviors within systems. Utilizing multi-layered security measures, including firewalls, intrusion detection systems, and behavior analysis tools, can further reduce risks.
2. Ransomware Evolution
Ransomware attacks are continuing to evolve, becoming more targeted and sophisticated. In 2025, ransomware may shift focus from individuals to critical infrastructure, healthcare institutions, government bodies, and large enterprises. Hackers now not only encrypt data but may also threaten to release sensitive information unless their demands are met.
How to Stay Safe: Back up your data regularly and ensure that backups are stored securely offline or on a separate network. Keep your operating systems and applications updated, and invest in robust endpoint protection solutions that can detect and block ransomware attacks before they encrypt data.
3. Deepfake Scams
Deepfake technology, which creates realistic but fabricated audio or video, is being increasingly used to impersonate executives, public figures, and even family members in a bid to commit fraud. In 2025, these scams are expected to become more convincing and harder to detect, posing significant risks to both businesses and individuals.
How to Stay Safe: Implement strong verification protocols for sensitive transactions. Educate employees and individuals about deepfake threats, encouraging them to double-check identity claims and be skeptical of unsolicited requests, even if they seem to come from trusted sources.
4. Cloud Security Vulnerabilities
As businesses and individuals continue migrating to cloud-based services, cybercriminals are exploiting misconfigured cloud platforms, insecure APIs, and weak access controls. These vulnerabilities can provide hackers with unauthorized access to sensitive data stored in the cloud.
How to Stay Safe: Use strong authentication mechanisms such as multi-factor authentication (MFA) and implement encryption for cloud data. Regularly perform security audits and ensure proper configuration of cloud services. Also, avoid storing sensitive data in public cloud spaces when possible.
5. IoT Device Exploits
With the growing number of Internet of Things (IoT) devices in use, ranging from smart home devices to connected vehicles, new attack vectors are emerging. IoT devices are often under-secured and may be exploited by hackers to launch large-scale attacks or compromise personal privacy.
How to Stay Safe: Secure IoT devices by setting strong, unique passwords, updating their firmware regularly, and segmenting IoT networks from other critical systems. Additionally, disable unused features and use firewalls to protect against potential breaches.
6. Social Engineering Attacks
Cybercriminals are increasingly using social engineering tactics, including phishing, pretexting, and baiting, to manipulate individuals into sharing confidential information. These attacks often exploit human psychology, making them particularly dangerous.
How to Stay Safe: Train employees to recognize and report phishing attempts and other social engineering tactics. Implement security policies that require individuals to verify requests for sensitive data, especially when they come through email, phone, or social media.
7. Supply Chain Attacks
Hackers are increasingly targeting supply chains as a means of infiltrating larger organizations. By compromising the systems of third-party vendors, they can access internal networks, steal sensitive data, or disrupt operations.
How to Stay Safe: Conduct regular security assessments and penetration testing on third-party vendors and partners. Implement strict access control measures and ensure that vendors comply with your security standards to minimize potential risks.
8. Quantum Computing Threats
While quantum computing holds great promise for advancing technology, it also poses a significant threat to traditional encryption methods. As quantum computing evolves, current cryptographic techniques may no longer be secure, leaving systems exposed to hacking.
How to Stay Safe: Stay informed about the latest developments in quantum-resistant cryptography. When quantum computing becomes more accessible, adopt new encryption standards designed to withstand the power of quantum attacks.
9. Biometric Data Breaches
With the increasing adoption of biometric authentication systems, such as facial recognition and fingerprint scanners, cybercriminals are increasingly targeting these systems for identity theft. If attackers gain access to biometric data, it could lead to irreversible security breaches.
How to Stay Safe: Use multi-factor authentication (MFA) alongside biometric authentication. Ensure that biometric data is stored securely in encrypted databases, and never transmit such sensitive data over unprotected networks.
10. Insider Threats
Insider threats, whether from disgruntled employees or compromised insiders, remain one of the most dangerous cybersecurity risks. Malicious insiders can cause considerable damage to an organization, stealing sensitive data or sabotaging systems from within.
How to Stay Safe: Implement strict access controls, limiting employees’ access to sensitive information based on job roles. Regularly monitor user activities and audit system logs to identify unusual behavior. Building a strong security culture within the organization can also help deter insider threats.
Conclusion
As the digital world becomes increasingly interconnected, cybersecurity threats will continue to evolve. In 2025, staying one step ahead of cybercriminals will require a proactive approach to security. By implementing advanced security technologies, adopting best practices, and ensuring continuous employee education, individuals and businesses can mitigate the risks posed by these emerging threats. It is crucial to stay informed, vigilant, and prepared to protect against the growing complexity of cyberattacks.